The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.

The MES Midmarket 100 is MES Computing's prestigious annual list recognizing forward-thinking technology vendors and service providers whose offerings support the growth and innovation of midmarket organizations.
This year's 2024 MES Midmarket 100 honors companies that successfully connect with mid-sized businesses and have a solid understanding that midmarket business IT needs often differ from those of large enterprises or small businesses.
MES Computing defines mid-sized businesses as meeting three of the four below criteria:
- Annual revenue of $50 million to $2 billion
- 100 to 2,500 total supported users/seats
- IT department from 5 to 50 employees
- An active IT budget of $750,000-plus
Vendors selected for the Midmarket 100 have shown a consistent commitment to helping customers utilize technology to help them thrive and succeed.
Profiles on the following pages include information provided by the honorees, including company and product descriptions as well as their responses to why they are a fit for the midmarket.
See the full list and information on each of the 100 companies here.
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
1Path Managed Services

1Path is a trusted end-to-end technology service provider for fully outsourced or co-managed IT services, cybersecurity expertise, innovative cloud solutions and digital transformation consultation. It is dedicated to equipping businesses with the knowledge and resources to excel in a digital-first world and offers a range of services tailored to growth-focused organizations. 1Path's offerings including fully outsourced or co-managed IT support, managed cloud solutions, and consulting and fractional advisory services.
"1Path's most prominent offering is the ability to stand up multiple industry-leading applications as part of our baseline tech stack that addresses end-user IT support and cyber security needs in a fully managed or co-managed environment. What sets 1Path apart from the competition is our ability to couple that approach with the highest level of customer service, support and ongoing technology guidance. Because we're flexible enough to work alongside your existing IT staff to augment certain capabilities or completely manage your IT environment from top-to-bottom, our offering is uniquely positioned to serve growing mid-market organizations."
Acer

Acer's commitment to supporting customers' technological needs and business growth is evident through its strategic partnerships, innovative solutions and best practices. By collaborating with partners, Acer ensures a comprehensive approach to addressing customer requirements. Whether it's leveraging cutting-edge technology, optimizing business processes or providing tailored solutions, Acer aims to transform challenges into new opportunities for growth. Among its midmarket offerings include Windows laptops, Chromebooks and monitors.
"Acer's approach integrates broad market reach, a diverse product lineup and a commitment to comprehensive solutions. This strategy enables Acer to turn potential challenges into fresh business growth opportunities."
Acronis

Acronis' top products for the midmarket include Cyber Protect Advanced, Cyber Protect Backup Advanced and Backup Advanced Microsoft 365.
"Acronis works exceptionally well for midsized clients due to its user-friendly setup and management capabilities consolidated under a single pane of glass. The platform's intuitive interface and streamlined workflows make it easy for IT teams with limited resources to quickly deploy and configure the solution. With all the essential functionalities, such as backup, security and patch management accessible from a unified interface, midsized clients can efficiently oversee and manage their IT operations. This simplicity reduces complexity, saves time and enhances operational efficiency, allowing midsized organizations to focus on their core business objectives while ensuring robust data protection and cybersecurity measures."
Acumatica

Acumatica is a cloud-based ERP solution purposely built to help small and midmarket companies thrive in today's digital economy. Acumatica's industry-specific business management solution is engineered to address real-world needs, featuring intelligent workflows and market-leading usability that enables companies to manage risk, anticipate disruption and seize new opportunities. Its product offerings include Acumatica Cloud ERP and Acumatica Industry Editions (Construction, Manufacturing, Distribution and Retail).
"Acumatica provides a scalable software solution that supports the needs of midmarket organizations. By emphasizing customer-centric business practices and growth-friendly licensing, Acumatica offers flexible deployment options, enabling companies to take control of their future. Recognizing that midsized companies are the lifeblood of the digital economy, Acumatica has a customer-driven approach to innovation, supported by twice-annual product releases with new features directly influenced by user feedback. Acumatica's channel-driven sales approach ensures that customers benefit from industry expertise and are supported by the comprehensive services and resources provided by Acumatica and its partners."
Addigy

Addigy simplifies Apple device management so that any IT administrator can easily manage and secure the Apple devices in their corporate network, regardless of their level of Apple expertise, with its Addigy Apple IT Management Platform.
"Using Addigy, IT teams can ensure employees' devices are always kept in an ideal and secure state. Addigy lets IT admins manage devices in real-time and provides out-of-the-box, zero-touch provisioning, asset management, monitoring and automated remediation, instant remote access, software deployment, configuration management and more."
Adler Advisors

As a full-service tech advisory, Adler Advisors is disrupting the way businesses buy, implement, and manage their technology investments. The company offers cybersecurity, contact center, and unified communications solutions.
"As former CIOs, engineers and technology sales executives, we know the process is too complicated, time-consuming and expensive. So we created something different. A better way. The Adler Way. Adler Advisors enhances our midmarket strategy by focusing on organizations with revenues of $50M-$2B, optimizing technology processes for businesses supporting 100-2,500 users. Our expertise as former CIOs and tech leaders allows us to simplify and reduce costs in technology acquisition and management. We add value by offering free program management, customer support, service escalations and tailored workshops, ensuring our solutions not only meet but exceed the IT needs within an active budget. Our commitment is to foster long-term partnerships through scalable, secure technologies and dedicated support, driving the success and innovation of midmarket organizations."
Adlumin

Adlumin is a security operations command center that simplifies complexity and keeps organizations of all sizes secure. Its innovative technology and seamless integrations create a feature-rich platform with everything sophisticated security teams need while empowering service providers and organizations of any size with collaboration and transparency for a coordinated, mature defense. With a vendor-agnostic approach and pre-existing integrations, Adlumin obtains security telemetry from across an organization to provide greater insights into security alerts and streamline workflows. Its midmarket products include Adlumin Managed Detection and Response and Adlumin Extended Detection and Response.
"The foundation of Adlumin's business is built on partnering with MSPs (Managed Service Providers), MSSPs (Managed Security Service Providers) and other resellers that service midmarket organizations. Adlumin was built with the midmarket in mind -- focusing on ease of use, transparency and collaboration with service providers to give any organization the enterprise-grade security that only the world's largest organizations have been able to afford. Adlumin avoids hidden fees that balloon final costs for customers by consolidating security needs into one feature-rich platform. Creating a foundation of transparency and trust is key to why Adlumin has been successful in selling to midmarket customers."
AgileBlue

AgileBlue is a global artificial intelligence-powered extended detection and response (XDR) and security orchestration and automated response (SOAR) platform that's proven to detect cyber threats faster and more accurately across entire digital infrastructures and clouds. The company provides 24/7 monitoring, detection, and response to cyber threats. AgileBlue's Sapphire AI streamlines SecOps (security operations) and SOAR processes, effectively reducing the risk of cyberattacks with rapid response capabilities and precise accuracy.
"AgileBlue's exclusive focus on the midmarket segment reflects a strategic decision to address the specific needs and constraints of companies within this particular market niche. By targeting mid-sized businesses, AgileBlue aims to assist organizations that may lack the resources or capabilities to maintain comprehensive security operations in-house. The Cerulean platform by AgileBlue is designed to be user-friendly and adaptable, recognizing that midmarket companies may not have dedicated cybersecurity teams or extensive technical expertise. This emphasis on usability ensures that even organizations with limited resources can effectively leverage the platform to enhance their security posture."
airSlate

AirSlate serves over 100 million users globally with its suite of award-winning eSignature, document management, and workflow automation solutions. Every solution is built upon a user-centric approach, delivering configurable experiences, simple collaboration, easy-to-use automations, and seamless integrations with existing systems. Cost-effective and quick-to-implement, airSlate's solutions turn document workflow automation into an accessible reality for midmarket companies. While airSlate's solutions benefit companies of all sizes, our primary focus is on midmarket firms and aiding their document workflow and digital transformation efforts. The airSlate platform is one of the highest-rated on G2, earning midmarket awards across several categories. Its products offerings include WorkFlow, SignNow, and pdfFiller.
"AirSlate is strategically positioning itself as a dominant player in the midmarket arena by employing a partner-driven approach to effectively reach midmarket customers and provide value-added services to clients. Our products seamlessly integrate with major platforms like Salesforce, NetSuite, and Microsoft Dynamics which is conducive to a channel strategy. Our vision is to be the premier partnership offering for partners looking to monetize eSignature and document workflow automation."
Allied Telesis

For 35 years, Allied Telesis has been delivering reliable, intelligent connectivity for everything from enterprise organizations to complex, critical infrastructure projects around the globe. In a world moving toward smart cities and the Internet of Things, networks must evolve rapidly to meet new challenges. Allied Telesis award-winning smart technologies, products, and services deliver efficient and secure solutions for people, organizations, and things, resulting in increased value and lower operating costs. Allied Telesis is committed to providing customers, from SMBs to enterprise, with solutions designed and built to the highest standards and quality. Its top midmarket products include the Its top midmarket products include Its top midmarket products include the TQ6702 GEN2-R Wireless AP Router, x530 Series Multi-Gigabit L3 Managed Switches, and Industrial Ethernet L2 PoE++ Switches (IE220 Series).
"Allied Telesis understands the distinct concerns many midsize organizations face in today's challenging IT and economic landscape, including limited budget and resources. Whether a company has one IT administrator or hundreds, Allied Telesis' innovative solutions lowers costs, eliminates complexity (with many all-in-one solutions), and frees up IT team management time. Allied Telesis provides midsized companies the simplicity and flexibility they need."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Arctic Wolf

The Arctic Wolf Security Operations Cloud brings order to the chaos and delivers the efficacy and efficiency that midmarket organizations want from their cybersecurity program, reducing cyber risk by enabling organizations to unify and derive actionable data from their litany of tools. Arctic Wolf can help solve the fundamental challenges of the skills gap and alert fatigue while giving customers a long-term, durable security posture improvement. By pioneering its unique cloud-native, multi-tenant security operations platform, Arctic Wolf drives down the likelihood and impact of security incidents so that overall risk can rapidly approach zero and be non-material to the customer. Its offerings for the midmarket include Arctic Wolf Managed Detection and Response (MDR), Arctic Wolf Managed Risk 3, aArnd ctic Wolf Managed Security Awareness.
"Our midmarket approach is guided by a principal of doing the most good and reaching the most organizations possible. We are not a boutique solution built for and used by a few niche markets, nor are we constrained by business models that primarily rely on selling and supporting only our own tools and technology. We have an assisted sell model with our channel community which is now >1,400 partners globally. Our team of sellers work hand in hand with the channel community and our mutual customers to sell our solutions."
Arista Networks

Arista Networks offers ease of use, easy deployment and management. Its product offerings require very little domain knowledge to implement and is designed to be implemented by a non-sophisticated IT manager with very little technical support. Commercial enterprise and SMB-type businesses have tight budgets and limited staff, yet are confronted with the same challenges that larger organizations have: multiple Wi-Fi, LAN and WAN network monitoring and management solutions that don't interconnect, rapid problem identification, mediation and resolution, and protection from increasing cyber threats. Its top midmarket products are Arista's Q-Series Next Generation Firewall, its Compact Wired POE Network Switches, and hi-availability Wi-Fi access points.
"Arista's Cognitive Unified Edge (CUE) offering is built for commercial enterprise users as an optimal edge as a service solution. CloudVision CUE provides plug-and-play management with built-in zero-touch automation, visibility and security. Unlike other disparate offerings, it leverages Arista's foundational CloudVision elements to deliver consistent customer experience, service activation, security posture and problem resolution."
ArmorPoint

ArmorPoint's cybersecurity solutions are crafted with the midmarket in mind, offering an integrated suite of cybersecurity program management solutions, spanning managed SOC (Security Operations Center), Managed Risk, and Managed Strategy. ArmorPoint delivers deep expertise fused with innovative technology to continuously assess and mature security postures, transforming cybersecurity from a defensive necessity to a strategic asset driving competitive advantage. Its offerings include ArmorPoint 360, Managed Strategy, and ArmorPoint XDR.
"ArmorPoint 360 is a comprehensive SOC platform tailored for the midmarket, typically catering to businesses with 250-2,000 employees. Our cloud-based solution utilizes critical cybersecurity functionalities like SIEM (Security Information and Event Management), EDR (Endpoint Detection Response), and MDR (Managed Detection and Response) to offer real-time threat detection, incident management, and more--all within a single dashboard. Designed for mid-sized companies seeking a scalable, efficient cybersecurity solution, ArmorPoint 360 enhances security postures by providing deep visibility and fast, effective threat response and remediation, ensuring robust management and mitigation of cybersecurity risks."
Aryaka Networks

Aryaka is a leading Unified-SASE-as-a Service provider, a SASE solution designed and built to deliver performance, agility, simplicity and security without tradeoffs. Aryaka meets customers where they are on their unique SASE journeys, enabling them to seamlessly modernize, optimize and transform their networking and security environments. Aryaka also empowers businesses to choose their preferred approach for implementation and management. Aryaka is a partner-led organization with 85 percent of revenue coming through sales partners, resellers and MSPs. Today, hundreds of multi-location businesses worldwide depend on Aryaka for cloud-based software-defined networking and security services. In addition to Unified-SASE-as-a-Service, the company offers Aryaka SmartConnect SD-WAN, and multi-cloud connectivity.
"Aryaka offers enhanced SD-WAN and SASE offerings designed for small to midmarket enterprises (SMEs). With entry pricing of under $150/site, Aryaka delivers comprehensive managed service capabilities including application optimization, network security, multi-cloud connectivity, and cloud-based observability and control, supported by lifecycle services management. SMEs face networking and security challenges, including budget, IT resources and operational complexity. To address midmarket issues, Aryaka combines in-house technology, a global private network, and 'as a service' delivery to offer cost-effective, managed secure networking. The holistic offer also eliminates vendor-provider finger-pointing that can negatively impact network performance and business operations."
Asigra

Asigra has been a trusted leader in ultra-secure, award-winning, on-premises cloud backup/recovery software since 1986. The company provides two data protection platforms that empower organizations to swiftly recover their data from anywhere, facilitated by an extensive network of IT solution providers. Asigra Tigris delivers ultra secure and highly capable backup/recovery that protects data from today's new breed of cyberattacks. Building on over 30 years of technology expertise, the all-new SaaSAssure SaaS application backup platform is the first to provide protection, recovery, security, and compliance of today's business-critical SaaS data. Its products include its SaaSAssure - SaaS Focused Data Protection solution, and Asigra Cloud Backup - Comprehensive Cloud-based Data Recovery Solution.
"The midmarket is the primary purchasing audience for Asigra's data protection product suite, which the company engages through its managed service provider network. Regarding go-to-market strategy, the company is building on this indirect sales model to increase market share."
Atera

Atera is an all-in-one, cloud-native, AI-powered IT management platform. Its industry-leading solution combines a user-friendly interface with multiple IT tools like RMM (Remote monitoring and management), help desk and ticketing, and patch management to empower technicians and teams and streamline organizational efficiency at any scale. While the platform has tools suitable for small businesses, Atera's main market focus is midmarket and enterprise; the platform offers an open API, a centralized, comprehensive suite of features that are highly customizable, alongside extensive automation capabilities of routine tasks. These are supplemented by a wide variety of integrations and marketplace add-ons to choose from.
"Atera is ideal for midsize businesses looking to optimize IT resources and leverage cutting-edge technology without breaking the budget. We aim to provide a balance between scalability, cost-efficiency, and cost predictability via our pay-per-technician business model; offer 24/7 live support across all pricing tiers to ensure immediate, personalized assistance; and prioritize both innovation and functionality as core values. Atera focuses on enabling our midmarket customers to efficiently manage their IT infrastructure, support remote or hybrid employees, and enhance the overall operational efficiency of their entire organization via streamlined workflows, automation, and extensive AI capabilities."
Auvik

Auvik is a cloud-based IT management platform that empowers IT teams to navigate change with less friction. The key is absolute simplicity: seamless deployment, an intuitive interface, and effortless automation. IT teams are able to proactively manage diverse networks, security devices, endpoints and SaaS applications. Users are able to work however and wherever they want. Auvik manages one million network devices and three million SaaS applications across 100,000 networks, and provides monitoring services for more than 10 million devices. Its products include Auvik Network Management and Auvik SaaS Management.
"Auvik's products are built with two types of customer profiles in mind -- midmarket organizations with internally staffed IT departments and MSPs whose clientele are composed of upper SMB and midmarket organizations. These often overlooked market segments have unique needs and price sensitivities. Because of the typical staffing scenarios of each of these segments, easy-to-use, out-of-the box functionality and features that automate menial network tasks are extremely important. Coupled with Auvik's focus on ease of use, our go-to-market model lends itself to fast, easy transactions and onboarding so busy IT teams can begin realizing value immediately.
Azul Systems

Azul is 100 percent focused on Java and provides the Java platform for the modern cloud enterprise. Millions of Java developers, hundreds of millions of devices and the world's most highly regarded businesses trust Azul to power their applications with exceptional capabilities, performance, security, and value. With Azul, Java developers, engineering and cloud teams from all organizations can increase app development and deployment, reduce cloud spend, and quickly capitalize on new revenue streams while reducing Java costs. Azul is ideal for all cloud-using Java organizations, enabling app modernization without the need to rewrite code and ridding codebases of dead code. Its offerings include Azul Intelligence Cloud, Azul Platform Prime, and Azul Platform Core.
"Perhaps more so than large enterprises, midmarket companies are under increasing pressure to deliver more with less, reduce expenditures and at the same time accelerate innovation. Azul's [go-to-market] strategy has always been focused on delivering solutions to customers, regardless of size and industry, that solve some of the biggest challenges businesses face today. That includes lowering Java software licensing costs, reducing cloud computing costs that are on the rise due to overprovisioning of services to meet high peak demands, and at the same time, increasing application performance and developer productivity."
Barracuda Networks

For more than 20 years, Barracuda has been making the world a safer place by keeping customers secure with smart, scalable solutions that provide rapid and effective protection for email, networks, data, and applications. Companies of all sizes worldwide trust Barracuda for proactive protection, unbeatable support, and total peace of mind. Barracuda protects customers in their digital transformation journey across all attack surfaces. Its solutions include email protection, network protection, data protection, application protection, and backup.
"One of Barracuda's strengths is our ability to offer choice for customers. That is a key part of supporting the evolving needs of midmarket customers. Whether customers are looking for hardware, software, or virtual solutions; working with a managed service provider or transacting in cloud marketplaces, we offer solutions that will work for them. Midmarket customers in particular are looking to reduce the number of disparate point products and vendors in their environment. The strength and breadth of Barracuda's security portfolio, designed with the midmarket in mind, helps customers get more technology solutions from a single vendor."
BCM One

Founded in 1992, BCM One is a leading next-generation communications and managed services provider. Serving over 20,000 customers worldwide and 5,000+ channel partners, BCM One offers telecom solutions supporting the critical network infrastructure of global businesses including: enterprise voice for Microsoft Teams, Cisco Webex and Zoom; global managed connectivity; UCaaS; SIP trunking; managed SD-WAN; and security and technology expense optimization.
"Midmarket companies tend to have increasingly complex network communications infrastructure but limited resources to manage it. BCM One solves this with our managed connectivity that aggregates various carriers on a global basis into one design, one bill, and one company to contact. We also deliver voice connectivity expertise that midmarket companies simply can't afford to staff in-house to help them seamlessly migrate from disparate legacy voice platforms to Microsoft Teams, Cisco Webex, or Zoom with enterprise-level functionality and service in 147 countries. And our nimble approach, compared to larger providers, enables midmarket companies to maintain critical agility."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Binary Defense

Binary Defense is a trusted leader in security operations, supporting companies of all sizes and industries to proactively monitor, detect and respond to cyberattacks. The company offers a personalized Open XDR approach to managed detection and response, advanced threat hunting, digital risk protection, phishing response, and incident response services, helping customers mature their security program efficiently and effectively based on their unique risks and business needs. Binary Defense gives companies of all sizes actionable insights within minutes -- not hours -- the confidence in their program to be resilient to ever-changing threats, and the time back that matters most to their business.
"With an ever-expanding attack surface, a resource-constricted team and budget, and an array of choices to shore up their security program, midmarket companies cannot protect their businesses alone against a constant barrage of cyber threats. In collaboration with our channel partners, Binary Defense personalizes a managed detection and response solution for midmarket companies by crafting an effective security strategy to accelerate detection, investigation, and response to potential threats while offering flexible pricing, scalability, and peace of mind. Binary Defense and their partners effectively address the specific needs of midmarket customers, building trust and long-term relationships."
Blue Mantis

Blue Mantis is a security-first, IT solutions and services provider with a 30-plus year history of successfully helping clients achieve business modernization by applying next-generation technologies including managed services, cybersecurity and cloud. Headquartered in Portsmouth, N.H., the company provides digital technology services and strategic guidance to ensure clients quickly adapt and grow through automation and innovation. Blue Mantis partners with more than 1,500 leading midmarket and enterprise organizations in a multitude of vertical industries and is backed by leading private equity firm, Abry Partners. Its midmarket products and services include GitMantis which leverages technologies from Blue Mantis partners, CloudTruth, the DevSecOps platform company that helps enterprise development teams manage their cloud configurations, and Nethopper, the pioneer of Kubernetes Application Operations Platform-as-a-Service (KAOPS). CloudTruth uses advanced digital twin technology to model workflows, manage configurations and fix leaked secrets from source code, deployment pipeline logs and security breaches. Nethopper is a cloud-native DevOps platform built for Kubernetes that allows development teams to securely manage any application in any cloud.
Blue Team Alpha

Blue Team Alpha is a veteran-owned, comprehensive cybersecurity force on a mission to secure and defend the digital world. It offers advisory, offensive, and technical services with deep roots and a specialty in incident management. With decades of experience handling breach investigations across all 16 critical infrastructure sectors, Blue Team Alpha has amassed the high-caliber talent in the cybersecurity industry. Over 65 percent of the company's experts are former nation-state-level employees from the Department of Defense, Department of Homeland Security, and other government organizations where they learned from the world's best cyber command. Blue Team Alpha's products and services include incident response, penetration testing, and Security Operation Center.
"Blue Team Alpha works with midmarket companies directly and through our channel partners (MSPs, MSSPs, VARs, TSDs) on proactive and reactive engagements. Blue Team Alpha is a market leader in incident response, assisting companies on their worst day. We work with companies proactively and provide offensive security, advisory services, and 24/7 monitoring solutions to better combat threat actors. Our security operators (primarily veterans out of DoD cyber command) provide expertise not only at a tactical level but also are willing to jump in with technical remediation, knowing most midsize organizations don't have the internal resources to address most issues."
BlueVoyant

BlueVoyant combines internal and external cyber defense capabilities into an outcomes-based, cloud-native platform by continuously monitoring the network, endpoints, attack surface, and supply chain, as well as the clear, deep and dark web for threats. The full-spectrum cyber defense platform illuminates, validates, and quickly mitigates threats to protect an enterprise. BlueVoyant leverages both machine-learning-driven automation and human-led expertise to deliver industry-leading cybersecurity to more than 900 clients across the globe. Its products and services include Microsoft Managed Detection and Response, Splunk Managed Detection and Response, and Supply Chain Defense.
"Midmarket clients make up a significant part of BlueVoyant's client base. Threat actors struggle to break into large enterprise organizations. Instead, increasingly, they target midsize enterprises, which may have weaker security. Cyber criminals will steal data from these organizations for a variety of reasons, including ransomware. But they don't stop there -- they continue to look for weaknesses within midmarket companies in order to then target larger enterprise organizations within their supply chain. A cyber incident can destroy a midsize enterprise organization's bottom-line and reputation. Our portfolio of offerings enables BlueVoyant partners to resell clients end-to-end cyber defense."
Blumira
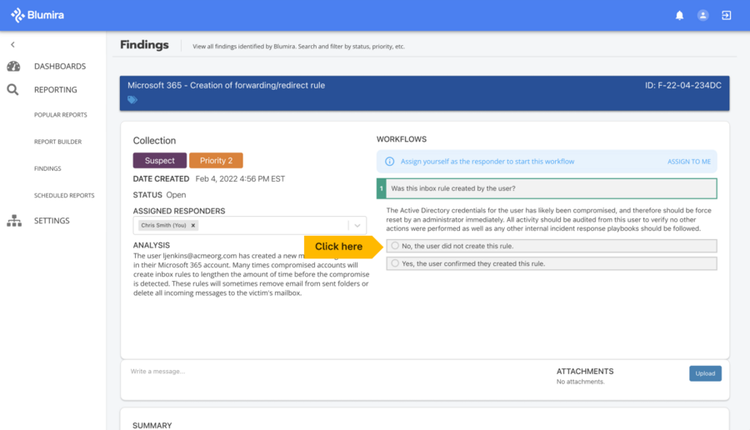
Blumira streamlines threat detection and response for lean IT and security teams with its unified SIEM and XDR platform. The solution provides logging, endpoint monitoring and automated response, resulting in faster alert resolution. The platform's guided playbooks and automation accelerate response times to swiftly neutralize ransomware and other attacks before damage occurs. Its flexible architecture integrates smoothly across diverse, hybrid technology stacks, covering the vital applications SMBs use every day. Blumira allows under-resourced IT staff to implement enterprise-grade protection with per-user pricing, avoiding many competitors' costly pricing structures. The company also offers free trial versions of its solutions which include Blumira XDR, Blumira SIEM, and Blumira Free SIEM.
"Blumira's midmarket strategy targets organizations with 50-2,000 employees, offering tailored cybersecurity solutions that balance robust protection with affordability. Blumira emphasizes simplified deployment and management, leveraging cloud-based analytics for real-time threat detection and response. The Blumira support team offers expert assistance to clients, aiding in platform setup, configuration and troubleshooting. [We] provide guidance on optimizing security posture, interpreting threat alerts and implementing best practices. Additionally, the team offers ongoing support to ensure customers effectively leverage Blumira's capabilities for robust cybersecurity defense. This support includes continuous innovation and adaptation to evolving cybersecurity threats and midmarket customer needs."
Brivo

Brivo is a global leader in cloud-based access control and smart space technology. It combines the best technology with the best service to deliver improved security for big and small companies, resulting in safer, smarter places to live, work, and play. Brivo created the cloud-based access control category over 20 years ago and the Bethesda, Md., based company has continued to break new ground in the industry since. Its products offerings include Brivo Access, Mobile Access Control Management, and Visitor Management.
"Most corporations deploy on-premises access control due to security concerns with the cloud. Brivo has to show more value from a business operations solution and has the opportunity to gain market share by tying in additional products to create solutions for its clients. Focusing on critical verticals provides other revenue opportunities and insight into industry trends and end-user problems that generate product development opportunities. Transparent, clear architecture documentation regarding how the solution resides on their network and communicates to the cloud is essential. This is important in converting traditional on-premises and/or hybrid solutions to a complete cloud system like Brivo."
Celigo

Celigo is a complete AI-enabled integration-Platform-as-a-service (iPaaS) that makes integration easy and simple, enabling businesses of all sizes to integrate their systems and accelerate digital transformation across the business with scale, reliability, and governance. With Celigo, business users and developers alike can integrate any business application and data to any other business application and automate and optimize business processes end-to-end using embedded business logic. Business teams can innovate faster and become more agile while IT has the tools to ensure unified best practices, data security, and scalability to meet the needs of the business today and in the future.
"Celigo's product and go-to-market strategy are focused on our target ICP (Ideal Customer Profile), which are midmarket businesses with annual revenues of $50M to $1B. Our focus on leveraging a no-code interface and AI to bridge the skill gap enabling business technologists and end users to create and manage integrations without IT is our key differentiator from traditional iPaaS solutions designed for development teams in large enterprises. Crucially, our simple and transparent pricing model based on endpoints and flows with no consumption fees provides mid-sized business with affordable and predictable costs."
Coalfire

Coalfire is a global services and solutions company that specializes in cyber advisory, assessment, and security. The company also develops cutting-edge technology platforms that automate defenses against security threats for the world's leading enterprises, cloud providers, and SaaS companies. Coalfire is the foremost provider of FedRAMP compliance assessments and penetration testing services in the United States. Its offerings include Cyber Advisory Services and Cyber Assessment Services.
"Midmarket companies, particularly those bound by industry and regional requirements for security compliance, turn to Coalfire for a one-stop shop for cyber assessment, advisory, and security. Financials, health care, payments, [and] tech companies at the midmarket stage are well poised to grow because they have product market fit but haven't 'maxed out.' We help these customers grow by assessing and building out their readiness [and] meet the security compliance regulations (HITRUST, HIPAA, FedRAMP, etc.) that govern these industries. Our red teaming services help customers proactively find their security gaps before hackers do."
ConnectWise

ConnectWise is a leading software company dedicated to the success of managed service providers (MSPs) that support millions of small and midsized businesses (SMBs) globally. With over 40 years of commitment to partner success, ConnectWise provides unmatched software, services, community, and integrations to fuel profitable growth. ConnectWise introduced the world's first true MSP platform, providing unprecedented flexibility and security with built-in artificial intelligence, robotic process automation, and machine learning capabilities. It all adds to efficient, productive end-to-end MSP solutions, including IT documentation, data management, cybersecurity, remote monitoring, and backup technologies. Its product offerings include ConnectWise Access Management and ScreenConnect.
"ConnectWise's midmarket strategy focuses on providing comprehensive software solutions and services to managed service providers (MSPs) that cater to small and midsized businesses (SMBs) worldwide. With a strong commitment to partner success spanning over 40 years, ConnectWise offers unparalleled software, services, community, and integrations to drive profitable growth for MSPs. At the forefront of innovation, ConnectWise introduced Asio, the world's first MSP platform incorporating revolutionary technologies such as AI, robotic process automation, and machine learning. This platform delivers exceptional flexibility and security, enabling efficient and productive end-to-end MSP solutions encompassing IT documentation, data management, cybersecurity, remote monitoring, and backup technologies."
Corero Network Security

Corero Network Security is a leading provider of distributed denial-of-service (DDoS) protection solutions to some of the largest SaaS companies, major enterprises, and hosting providers, specializing in automatic detection and protection solutions with network visibility, analytics, and reporting tools. While a substantial portion of its client base and revenue comes from the midmarket sector, Corero's scalable technology allows it to easily address the needs of large enterprises as well. Corero SmartWall ONE protects against external and internal DDoS threats in complex edge and subscriber environments, ensuring internet service availability. In addition to Corero SmartWall ONE, its product lineup includes Corero SecureWatch Managed Services, and Corero DDoS Intelligence Service.
"A main business driver for companies looking to purchase DDoS protection solutions is the ability to generate revenue by adding it into their product portfolio. In response to this, our team developed DDoS Protection-as-a-Service (DDPaaS) Resell-In-A-Box. This makes it as easy as possible for service providers to justify and launch a new DDoS protection service offering from a product management and marketing perspective. This includes a financial model calculator with pricing examples, sample content for brochures and web pages, marketing campaign and project plan, and 'best practices' examples from other service providers.
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Coro

Coro protects hundreds of thousands of SME and midmarket companies whose limited budgets, lean IT teams and lack of cybersecurity expertise make them prime targets for cyberattacks. To address these challenges, Coro created a new cybersecurity paradigm with the launch of Coro 3.0, the world's first modular cybersecurity platform. Coro 3.0 consolidates critical security capabilities into a single platform that's easy to manage, reduces operational workload and complexity, and scales as you grow. Coro eliminates the security gaps caused by multiple tools in the security stack while offering the lowest total cost of ownership on the market today.
"Coro designed its platform from the ground up to address the security challenges faced by midmarket organizations. With limited resources, cybersecurity is typically handled by the company's IT staff, who quickly become overwhelmed by the complexity of managing multiple security tools. Coro's strategy is to offload work from lean IT teams by simplifying and automating cybersecurity. Coro consolidates critical security capabilities into a single platform, automates threat remediation, reduces operational workloads caused by managing multiple software agents and dashboards, and eliminates the extra training required to work with multiple point products, all at the industry's lowest cost of ownership."
Corsica Technologies

Corsica provides an integrated IT and cybersecurity strategy customized to fit your goals and technology roadmap. The company offers cybersecurity solutions, managed services, digital transformation, resale services, and one-off technology projects. Corsica unifies any combination of these services into a complete, seamless solution. Its focus is on personalized customer service, which is why they primarily serve regions where their teams live. Corsica specializes in the banking, finance, manufacturing, health care, nonprofit, and education industries. It provides services for cybersecurity, IT support, and digital transformation.
"Corsica Technologies specializes in providing managed technology and security expertise for midmarket clients. Our focus is on providing a technology framework to guide clients in securing and connecting their digital assets in support of their business goals. Our vision is to protect, educate and advance businesses through exceptional technology and security expertise. Our midmarket strategy focuses on a specific ICP consisting of businesses with 100-500 users, a revenue of $25M-300M, and in regulated industries like financial services, health care/long-term care (clinics and hospitals), manufacturing, education, nonprofits and government."
Cradlepoint (part of Ericsson)

Cradlepoint, part of Ericsson, the global leader in cloud-delivered LTE and 5G wireless network and security solutions, enables the freedom to connect people, places, and things that drive more experiences, more ways to work, and better business results anywhere. Through its unified NetCloud platform, Cradlepoint delivers a solution that offers the agility of 5G, the control of private networks, and the security of zero trust to transform business operations and customer service at fixed sites, in vehicles, with IoT devices, and beyond. Cradlepoint NetCloud SASE enhances the simplicity of enterprise-class network security for even the leanest IT organizations. It also offers its Secure Wireless WAN Solution for branch, IoT and vehicles.
"Many organizations lack adequate internal IT staff as businesses cut costs. As networks become more complex, adding mobile, IoT, branch. AI/ML applications that need consistent connectivity, the reach of the network (WAN) deepens and 5G/cellular becomes the best option to connect where wires can't. Lean IT teams can leverage NetCloud SASE to deploy a zero-trust network, at scale, in as little as six minutes, addressing the current industry void for simplified networking and security in dynamic environments."
CybeReady

CybeReady stands as a global leader in cybersecurity awareness training, representing a readiness-first approach redefining how organizations are prepared for real cyberattacks. Its mission is to equip companies with a data-driven methodology ensuring training program effectiveness. CybeReady helps midmarket organizations achieve an exceptional combination of risk reduction, an engaging learning experience, and cultural impact while addressing compliance challenges. The company offers social engineering simulations and learning, cybersecurity awareness training, and internal communications centers.
"At CybeReady, we're reshaping the cybersecurity training landscape. We recognize the relentless challenges organizations face from hackers exploiting vulnerabilities to the overwhelming tasks handled by security teams. Our innovative approach doesn't just address these challenges; it revolutionizes how companies prepare for real cyberattacks. By prioritizing readiness and leveraging data-driven methodologies, we equip organizations with the tools and knowledge needed to effectively mitigate risks and foster a security-conscious culture. With our comprehensive SaaS platform, available in 42 languages, we ensure that cybersecurity training is not only impactful but also accessible to teams worldwide."
Cybersafe Solutions

Cybersafe knows that a typical client environment can range in industry, size and team. Some of their clients have fully outsourced IT, some have a combination of both in-house and outsourced, and others have fully operational IT and security teams. Cybersafe understands that it's not a matter of if your systems will be breached, it's when. Cybersafe's comprehensive MDR solution provides real-time visibility, detection, response and containment across corporate endpoints, networks, and clouds. The company delivers a multilayered, defense in-depth solution bringing visibility and adding value to each of those scenarios, allowing it to be a force multiplier for its clients and its overall security program.
CyFlare

CyFlare delivers advanced cybersecurity solutions designed specifically for the midsize enterprise market. Its platform leverages high-degree automation (at 98 percent) and exceptional accuracy (97 percent true positives) to streamline threat detection, response, and remediation. This empowers businesses to achieve robust protection without straining internal IT resources. The company's focus is on simplified UX (user experience) and integration with existing tool sets to ensure immediate value within existing workflows. Its product portfolio includes CyFlare Managed Extended Detection and Response (mXDR), CyFlare Managed Endpoint Detection (mEDR), and CyFlare Vulnerability Management.
"CyFlare's midmarket strategy prioritizes rapid deployment, superior automation, and a simplified user experience. We deliver industry-leading security solutions designed for midsize enterprises that demand robust protection without the complexity or resource strain often associated with enterprise-grade cybersecurity."
DYOPATH

DYOPATH is one of the largest privately held MSPs in the United States and brings over 26 years of experience in technology, cybersecurity, and end-to-end solutions to support their clients with all of their IT needs. DYOPATH now has locations across the U.S. and Mexico and supports companies domestically and abroad. No matter the industry, DYOPATH helps organizations manage their risk, technology, and teams more effectively. The company provides cybersecurity, cloud services, and managed services.
"DYOPATH specializes in cultivating strategic partnerships with organizations that thrive on the symbiotic relationship between business and technology. Through streamlining operations and integrating efficient people, processes, and tools, DYOPATH creates a digital ecosystem marked by continual growth and innovation. This evolution results in significant enhancements within your organization carrying you toward your greater goals. Our business-first approach is unique, just as every organization we partner with is unique, and our process is proven and powerful. From solution design to onboarding to service integration, we guarantee a distinct journey marked by seamless leadership and effective IT maturity enhancement."
Eaton

Eaton is an intelligent power management company dedicated to improving the quality of life and protecting the environment for people everywhere. The company is guided by its commitment to do business right, to operate sustainably and to help its customers manage power today and will into the future. Capitalizing on the global growth trends of electrification and digitalization, Eaton is accelerating the planet's transition to renewable energy, helping to solve the world's most urgent power management challenges, and doing what's best for its stakeholders and all of society. The company's products include uninterruptible power supplies, rack power distribution units, and power management software and services.
"Eaton's midmarket strategy is built on the company's ability to deliver innovative power management solutions that address a range of challenges for end customers while driving profitable business for its partners. With a dedicated sales team focused on distributed infrastructure and an expanding product portfolio, Eaton is meeting the market's need for power management technologies that serve a broad variety of midmarket use cases."
Echelon Risk + Cyber

Echelon Risk + Cyber stands out as a premier cybersecurity professional services firm, delivering tailored solutions designed to meet the unique needs of every client. Its team collaborates closely with individuals across mid-to-large sized companies in diverse sectors, offering strategic and tactical cybersecurity solutions. Echelon Risk + Cyber offers offensive security and testing, cyber risk and compliance, vCISO-led Security Team-as-a-Service (STaaS), as well as comprehensive cybersecurity strategy development and defensive security services.
"At Echelon, we're here to be your trusted ally in safeguarding your digital assets. Our commitment? Providing top-tier service without breaking the bank, tailored precisely to your cybersecurity needs. Our team is a dynamic mix of cybersecurity experts, with one mission: fortifying your cyber resilience. We steer clear of one-size-fits-all approaches. Instead, our focus is on crafting personalized cybersecurity solutions that align seamlessly with your business objectives. For mid-size enterprises like yours, we go the extra mile to ensure our service plans flex and adapt to meet your specific requirements, ensuring a perfect match for your budget and cybersecurity aims."
Entara

Founded in 2001, Entara is an extended service provider focused on providing cutting-edge technology and security solutions to companies in regulated industries. With roots in serving the electronic trading market, Entara is known for growing with the pace of technological change and the developing needs of its clients. As a security-first company, it serves as a trusted advisor to clients and works with organizations who value a proactive and mature security strategy. Entara also provides breach remediation services to companies of all sizes and takes decimated environments to get them back up and running within hours, not weeks. Entara offers endpoint management and end user support, cybersecurity retainer, and micro-segmentation.
"Entara's midmarket strategy focuses on clients who are held to compliance standards by their industry or clients, including health care, financial, and insurance companies based primarily in the U.S. We know that cybersecurity is pivotal for companies of all sizes, but those in the midmarket may be limited by budget or internal expertise. To support midmarket clients, we provide services that help them build a roadmap that will increase their resilience over time and in line with their budget. We also use our frontline incident response experience to help midsize companies prioritize the most pivotal cybersecurity services they need to implement."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
eSentire

ESentire is the cybersecurity leader in managed detection and response (MDR), protecting its customers and partners' end-customers from known and unknown cyber threats for 23 years with award-winning MDR, exposure management, and digital forensics and Incident Response services that prevent business disruption. eSentire drives deep, multi-signal investigation across cloud, network, endpoint, log, and identity sources for complete attack surface coverage for on-premises, hybrid, and cloud environments. Our innovative XDR Cloud platform, 24/7 threat hunting, and proven security operations expertise, combine to provide an all-in-one solution that helps organizations of all sizes anticipate, withstand, and recover from cyberattacks. Its product portfolio includes the eSentire Agent, eSentire MDR for Microsoft, eSentire MDR for Cloud (Cloud Security Posture Management, Cloud Workload Protection Program, and AWS for Network).
"With deep knowledge of midsize organizations, including critical infrastructure entities, eSentire delivers best-of-breed security solutions tailored to meet the unique needs of businesses with small security teams and lean budgets. Our 24/7, multi-signal MDR services, comprised of our AI-based Extended Detection and Response technology, elite security experts, and real-time threat intelligence, enable us to detect, protect, and rapidly respond to cyberthreats. In October 2023, eSentire introduced the eSentire Agent as a premier MDR protection platform specifically for midsize enterprises and SMBs seeking powerful, affordable prevention, detection, investigation, and response capabilities as part of an all-in-one, 24/7 security solution."
ESET

ESET offers "highly customizable cybersecurity solutions with minimal impact on performance, that identify and neutralize known and emerging threats before they can be executed, support business continuity, and reduce the cost of implementation and management." Its product offerings include ESET Protect Advanced, ESET Protect Complete, and ESET Protect Enterprise.
Why ESET is a fit for the midmarket: "Ease of use, single pane of glass, customizable reporting, high detection rates, low false positives and fast performance. Complimentary technical support is available based out of San Diego, Calif."
ExaGrid

ExaGrid provides tiered backup storage with a unique disk-cache Landing Zone, a long-term retention repository, the only tiered air gap for ransomware recovery, and a scale-out architecture. ExaGrid's Landing Zone provides for the fastest backups, restores, and instant VM (virtual machine) recoveries. The Repository Tier offers the lowest cost for long-term retention. ExaGrid's scale-out architecture includes full appliances and ensures a fixed-length backup window as data grows, eliminating expensive forklift upgrades and planned product obsolescence. ExaGrid offers the only two-tiered backup storage approach with a non-network-facing tier (creating a tiered air gap), delayed deletes, and immutable objects to recover from ransomware attacks. Its product lineup includes ExaGrid Tiered Backup Storage Appliances.
"ExaGrid Tiered Backup Storage offers what midmarket to enterprise organizations need for their backup storage: a scale-out architecture that allows organizations to add appliances as their data grows, so they only pay for what they need, as well as a backup storage solution that is ready for ransomware recovery. ExaGrid works with more than 25 industry-leading backup applications with the easiest installation/management, and lowest cost up front and over time. ExaGrid's product line consists of 2U appliance models offering rack space efficiency for savings on rack storage, power and cooling costs while accommodating large data backups and future data growth."
Forcepoint

Forcepoint simplifies security for global businesses, delivering modern cybersecurity by proactively safeguarding critical data. Forcepoint's all-in-one, truly cloud native platform makes it easy for enterprises to adopt Zero Trust and prevent the theft or loss of sensitive data and intellectual property no matter where people are working: in the office, at home, in the coffee shop, airports, and beyond. Based in Austin, Texas, with regional headquarters spanning across the globe, Forcepoint creates safe, trusted environments for customers and their employees in more than 150 countries. The company's offerings include Forcepoint ONE Data Security and Forcepoint Data Security Posture Management (DSPM).
"We are uniquely focused on delivering data security everywhere, tackling security challenges head-on for modern distributed enterprises. Our data-first strategy is centered on cloud-delivered security and connectivity, providing our partners with differentiated offerings that help businesses today while addressing their biggest challenges, such as IP protection and compliance. As a channel-led organization, relationships with partners around the world are integral to our success, with nearly all our deployments are completed by our partners. Our midmarket strategy is centered on the guiding principles of simplicity, growth, and partner-led services to ensure enterprises have the security expertise and support needed for success."
Fortinet

The Fortinet Security Fabric spans the extended digital attack surface and cycle, enabling self-healing security and networking to protect devices, data, and applications. With midsized organizations feeling the cybersecurity skills gap pinch, the Fabric's broad, integrated, and automated platform extends their team's capabilities allowing them to focus on innovative initiatives. The Fabric is based on three attributes: detect threats and enforce security everywhere; close security gaps and reduce complexity, and enable faster time-to-prevention and efficient operations. Additionally, with one operating system (FortiOS), the Fabric supports granular use cases with more deployment models than any other solution. These include physical, virtual, cloud, and X-as-a-Service environments. And it encompasses the industry's broadest ecosystem and product portfolio, spanning endpoints, networks, and clouds. Fortinet's midsize enterprise offerings include FortiManager/Analyzer, and its SD-WAN solution.
Galactic Advisors

Galactic Advisors serves MSPs delivering Compliance as a Service that is focused on cybersecurity auditing, penetration testing and executive-level data reporting. In addition, the company empowers tech teams with incident response and security operations training. Its goal is to change the conversation around compliance, emphasizing its importance and impact on organizational scalability and security.
"Galactic empowers midmarket organizations with clear, approachable reporting, enabling effective boardroom engagement. In addition, we offer a scalable compliance program, allowing midmarket businesses to expand their compliance efforts seamlessly. Our high-impact, executive-focused results provide clear evaluations of risk, facilitating informed decision-making."
GoTo Technologies

Purpose built to help businesses grow, GoTo Technologies offers a cloud-based phone system, with customer engagement tools and contact center solutions to modernize business communications, centralize interactions, and elevate customer experiences. It also provides remote IT management and support to assist businesses of all sizes with secure and affordable IT solutions for remote and hybrid work. GoTo has helped tens of thousands of midmarket companies grow their business with a cloud phone system with hundreds of enterprise-grade features, contact center solutions, and AI-powered tools. It also offers remote IT Solutions with AI for mid-sized companies and budgets with 99.999% uptime Its product portfolio includes GoTo Connect, GoTo Contact Center Complete, and GoTo Resolve.
"We help [midmarket] companies consolidate business communications and IT support solutions with one trusted provider resulting in cost savings, increased productivity, better customer experiences and reducing strain on IT teams. Affordable price points mean businesses can find solutions to fit their budget and easily scale as their needs change without costly fees, disruptions, or downtime. We provide practical, easy to use AI tools to help improve employee productivity, speed up customer resolutions, personalize interactions and enable easy IT support across all customers. GoTo can customize solutions, with an implementation services team willing to work with MM businesses for modifications."
Gradient Cyber

Gradient Cyber provides a leading midmarket Managed Detection and Response (MXDR) solution which bolsters your cybersecurity posture, compliance, and business resilience; pinpointing and halting attacks before they lead to financial setbacks, operational disruptions, data breaches, or reputational harm. Its open XDR platform integrates a variety of endpoint, identity, network and cloud data sources. Advanced analytics connect and contextualize data signals into prioritized alerts which are vetted by cyber analysts and converted into response and remediation action. Combined with its 24x7 SOC, and white-glove model Gradient Cyber, ensures high customer satisfaction at a fraction of the cost of alternative approaches.
"Building and maintaining a Security Operations Center (SOC) is a resource-intensive and very costly endeavor, often beyond the reach of many midmarket businesses. An MXDR service should provide the benefits of a fully-functional, certified SOC without the associated overhead. Our offering includes access to the latest in cybersecurity technologies and skilled analysts, eliminating the need for extensive investment in training or infrastructure. For businesses grappling with the challenge of finding, hiring, and retaining cybersecurity talent, SOC-as-a-service is a game-changer."
Horizon3.ai

Autonomous penetration testing enables organizations to see themselves through the eyes of the attacker, allowing small to mid-sized companies to continuously assess their IT infrastructures, quickly identify exploitable weaknesses, and verify their remediations are effective. Horizon3.ai leverages its expertise, data, and insights to deliver the NodeZero platform to organizations so they can preemptively discover weaknesses in their infrastructures before attackers do. NodeZero gives IT administrators and security professionals 'superpowers' to operate like experienced ethical hackers and acts as a force multiplier for midmarket, MSPs, and MSSP partners.
"With small and midsize organizations increasingly becoming the focus of attackers, an autonomous penetration testing platform that doesn't take weeks to execute and doesn't break the budget is what smaller companies are in need of. And NodeZero is just that. With a few simple clicks, organizations can easily assess their networks in a matter of hours. And the platform helps clients focus on fixing problems that can actually be exploited, saving time and resources. With Horizon3.ai, customers establish a purple team culture allowing them to continuously evaluate their security postures by identifying, fixing, and verifying exploitable weaknesses are resolved."
Huntress

Huntress is a cybersecurity leader focused on protecting and empowering small-to-medium-sized enterprises. Combining the power of the Huntress Fully Managed Security Platform with a fully staffed 24/7 Security Operations Center (SOC), Huntress provides the technology, services, education, and expertise needed to help companies overcome their cybersecurity challenges and protect critical business assets. Founded in 2015 by a group of former National Security Administration (NSA) operators, Huntress has more than doubled over the past couple of years to support 4,300 partners and more than 105,000 organizations and now protects more than 2 million endpoints. Its product and service portfolio includes its Managed Endpoint Detection &Response (EDR), MDR for Microsoft 365, and its Security Awareness Training.
"Huntress is supporting midmarket companies through its MSSP and MSP channel partners and has had initial success in the [midmarket] healthcare vertical."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
HYPR

HYPR fixes the way the world logs in. HYPR True Passwordless MFA platform eliminates the traditional trade-off between security and user experience by providing uncompromising assurance and consumer-grade experience. The result is that organizations decrease the risk of an attack, increase positive user experience and lower operational costs. With HYPR, customers are able to completely eliminate shared secrets with its passwordless authentication approach, and thus eliminate push attacks by putting the user in control. For midsize companies with limited resources, HYPR can be installed rapidly and is fully integrated with leading single sign-on providers such as Okta, Google, Azure, Ping Identity, and more. The deployment process is straightforward: users are invited via a magic link that downloads the HYPR app, and they enroll. The end result is 300 percent faster access than legacy password logins such as password and desktop MFA. It's seamless from desktop to cloud with the same login experience everywhere.
Hyve Managed Hosting

Hyve strives to be a genuine partner, not just a provider. By understanding its customers' business needs, challenges, and prospects, the company uncovers opportunities customers didn't even know existed. The teams at Hyve work directly with customers throughout their journey, eliminating the need for transfers to anonymous engineers and automated call centers. Among its offerings, Hyve provides single tenant cloud, dedicated servers, and multi-tenant cloud.
"Our expert team can handle any issues, with technical support ensuring smooth operations in the background."
JumpCloud

The JumpCloud directory platform offers premium identity, device, and access management for small and medium-sized enterprises (SMEs) by integrating MFA, SSO, directory services, unified endpoint management, mobile device management, passwordless authentication, remote support, and more into a single tool. This eliminates the need for multiple endpoint security solutions even in mixed device environments (macOS, Windows, Linux) and gives small and medium-sized organizations an easy and cost-effective approach to managing user identities and devices. JumpCloud has been adopted by over 200,000 SMEs, has over 6,000 paying customers, and over 2,000 MSP partners in 160 countries. Its offerings include JumpCloud Directory Platform, JumpCloud Go (phishing-resistant passwordless authentication add-on), and Device Enrollment and Mobile Device Management.
"JumpCloud's mission for SMEs is to 'Make Work Happen.' Recognizing that smaller organizations often don't have the budget or staff of their enterprise counterparts, JumpCloud's directory is designed for the unique needs of SMEs. It's flexible, allowing easy tweaks to meet the specific needs of SMEs across mixed device environments and a mix of legacy and cloud-forward systems. For SMEs turning to MSPs to manage IT, JumpCloud's MSP offerings offer a powerful, unified tool with multi-tenancy for managing clients, making their access to IT resources easy and keeping their sensitive data secure."
Kaseya

Kaseya's IT Complete product suite is comprised of industry-leading solutions from its family of companies: Unitrends, RapidFire Tools, Spanning Cloud Apps, IT Glue, ID Agent, Graphus and RocketCyber. Kaseya's solutions were created for the multi-functional IT professional, who is often responsible for all business needs at a midsize enterprise -- from backup and patch management to compliance. Through its workflow and solution integrations, IT Complete eliminates the "space between," or the valuable time IT professionals waste moving between disparate applications and processes. Kaseya's solutions allow internal IT teams to free up resources, enabling those teams to better serve their organization.
Kissflow

Kissflow is a low-code application development platform specifically built to handle the challenges of middle office automation. It has the power and versatility to help IT teams burn through their application backlog at an extremely quick pace. However, it is also simple enough for non-IT power users to build their own workgroup applications. On top of all of this, there is a governance layer that keeps IT leaders in control of the entire platform. Kissflow provides citizen development (no-code automation), low-code app development, and custom workflow management. Kissflow integrates with major CRM, ERP, accounting, and project management tools.
"Kissflow understands that mid-sized businesses often have unique requirements and workflows with a moderate scale of operations and resources. As part of its strategy, it offers the ability to build, manage, automate, and tailor workflows according to specific needs; high scalability and capacity to handle increased workload and complexity without requiring a significant overhaul; pricing based on usage to accommodate organizations of all sizes; an easy-to-manage governance layer that keeps even smaller IT teams in control; and an enablement professional services team to get midmarket organizations up and running quickly."
Lenovo

Lenovo continues to excel in diverse technology sectors, focusing on innovation and sustainability. In 2024, the company is leveraging AI, IoT, and 5G to enhance its product lineup, spanning laptops, PCs, servers, and smart devices. Key initiatives include advancing datacenter solutions for hybrid cloud environments, reinforcing its leadership in the PC market, and expanding into emerging areas like edge computing and AI-driven devices. Lenovo prioritizes customer-centricity, striving to meet evolving needs with reliability and performance. With a commitment to eco-friendly practices, its fostering a greener future while maintaining its position as a global tech frontrunner. Among its midmarket products are datacenter solutions, end user compute devices, and software and services.
"Lenovo's midmarket strategy revolves around offering high-quality, affordable technology solutions tailored to the needs of small and medium-sized businesses (SMBs). [We] aim to provide a comprehensive range of products, including laptops, desktops, servers, and networking solutions, coupled with robust customer support and service packages. Lenovo focuses on delivering reliable performance, security features, and scalability -- empowering mid-sized enterprises to enhance productivity and competitiveness. Through strategic partnerships and channel programs, Lenovo seeks to expand its reach and strengthen its position as a trusted technology partner for midmarket businesses worldwide."
Lightyear

Lightyear's software allows small to mid-sized to enterprise businesses to buy and manage their network services (internet, WAN, data center, voice/phone) on a ridiculously easy-to-use online platform. With Lightyear, customers can configure services, get quotes, pick vendors, sign contracts, monitor implementations, handle renewal shopping, and manage their entire network inventory in one vendor-neutral platform. Hundreds of enterprise users trust Lightyear with all of their network procurement needs, including those at Louis Vuitton, Palo Alto Networks, Starwood, StockX and Element Solutions as well as several ISPs (Internet Service Providers).
Mitsogo

Established in 2013, Mitsogo Inc. is the parent company of Hexnode, a leading unified endpoint management provider headquartered in San Francisco. Mitsogo maintains a strong commitment to innovation, continuously addressing the evolving needs of the modern enterprise landscape. Serving organizations of all sizes and industries, Mitsogo delivers scalable solutions tailored to suit various endpoint management requirements. As a leading unified endpoint management solutions provider, Mitsogo brings a fresh perspective on how businesses function with a vision to empower the digital workplace.
"The feature expansion of Hexnode directly relates to the security and overall employee experience in the workplace. The cybersecurity landscape of the current times also calls for businesses to invest in scalable solutions that are easy to integrate with other IT solutions and provide them with 360-degree visibility of all their assets. Hexnode has introduced security hardening features like patching and encryption along with plans to expand the OS (operating system) support to Linux and Apple Vision OS. Hexnode's five-tier pricing plan helps businesses of all sizes choose a budget-friendly solution that meets all their requirements."
MobiDev
Providing high technology expertise, understanding business goals before engineering, and caring about the result - this is how MobiDev works. MobiDev is a software development company that creates solutions for U.S., Canadian, and European businesses. The company focuses on developing new software products and helping existing ones evolve. MobiDev has business units in the U.S. and the UK. Research and development centers are located in Poland and Ukraine, with 300-plus engineers. It offers AI consulting, software engineering, and tech strategizing.
"At MobiDev, we specialize in modernizing outdated tech into scalable, secure, and innovative systems that align with current trends and propel you into new markets. We do it fast and we do it right. With MobiDev, clients' investments in product modernization do more than update old systems -- they unlock new opportunities for growth, enhance customer satisfaction, and solidify your market leadership, ensuring clients' company's profitability and long-term success."
N-able

N-able fuels IT professionals with powerful software solutions to monitor, manage, and secure their systems, data, and networks. Built on a scalable platform, N-able offers secure infrastructure and tools to simplify complex ecosystems, as well as resources to navigate evolving IT needs. Its products build ease and efficiency into all functions of IT, from endpoint management to backup and security, all from a single web interface. N-able's midmarket offerings include Cove Data Protection, from N-able, N-able N-central -- a unified endpoint management solution, and N-able Endpoint Detection and Response.
"IT departments of all sizes need the right tailored solutions to meet them where they are. N-able helps level the playing field and provide products and solutions powerful enough for larger IT departments or those at the beginning or in the middle of their growth journey. N-able helps deliver everything they need to streamline their IT operations, including robust, integrated products to monitor, manage, and protect data to optimize their business and help them grow with a price tag that reflects their company's budget."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Nerdio

Nerdio is a Microsoft partner empowering managed service providers, systems integrators, and enterprise IT professionals to deploy, manage, and optimize Windows 365 and Azure Virtual Desktop environments. Leveraging Azure Virtual Desktop and/or Windows 365, organizations can set up a scalable and flexible environment to accommodate diverse workloads and reduce costs with pooled, multi-session resources. Nerdio's management platforms for Azure, Nerdio Manager for Enterprise and Nerdio Manager for MSP, enhance Microsoft's native virtual desktop services and allow IT administrators to seamlessly provision and manage them side by side.
"Nerdio Manager tackles the challenges faced by mid-sized enterprises regarding the costs of cloud infrastructure and resources. For companies lacking adequate staffing or expertise in Azure Virtual Desktop (AVD), Nerdio offers efficient solutions to maintain their End-User Computing (EUC) environments. Nerdio automates the intricate processes of Intune, Azure, and AVD, enabling midmarket firms to swiftly configure and manage AVD on a day-to-day basis, even without extensive expertise. We also support channel partners catering to midmarket enterprises, ensuring they receive optimal support and necessary resources for their AVD migration efforts."
Netography

The Netography Fusion platform was designed to help organizations move beyond the traditional threat-centric detection model (which generates high volumes of low-value alerts of potentially malicious content and activity) and embrace a compromise-centric detection model (which generates low volumes of high-fidelity alerts on actual compromises). Security, cloud, and network operations teams benefit with context-rich alerts that identify activity that should never happen, rather than detecting a potential issue. Netography's market focus is to enable cloud-forward companies to quickly and effectively see what their applications, data, and workloads are doing and what's happening to them across their multi-cloud and hybrid networks.
"Netography's strategy is to target midmarket companies that are cloud-forward in their approach to their network infrastructure, as they have fewer tools to provide critical observability of multi-cloud and hybrid networks. They also are eager to move on from legacy detection-centric technologies that were engineered for network environments that no longer exist, and want to deploy cloud-native, 100% SaaS solutions."
Nitel

Nitel is a leading Network-as-a-Service (NaaS) provider. Nitel aims to simplify the complex technology challenges of today's enterprise organizations to create seamless and integrated managed network and security solutions to help customers meet the demands of digital transformation. As Nitel solves customers' complicated IT challenges, they can leverage the cloud with greater performance and security, and in turn have the freedom to focus on other critical business issues. Nitel's products and services include Aggregated Global Access, Global SASE: SD-WAN, and Global SASE: Managed Security.
"Nitel's focus has been to address the critical needs of midmarket business customers through a customer-centric managed services approach. At the center of Nitel's strategy is the understanding of the issues these businesses face. Increasingly mobile workforces have created new application performance and security challenges. IT organizations of midmarket companies don't have the breadth of expertise required to support the needs of those businesses. International requirements present specific challenges that midmarket companies struggle to support."
Nutanix

The Nutanix Cloud Platform is designed to meet the needs of midsized companies whose IT strategies must accommodate applications and data residing in traditional on-premises data centers, in multiple public clouds, and at the edge, which drive additional cost and complexity to manage. The Nutanix Cloud Platform meets these needs, while delivering the simplicity and agility of public cloud alongside the performance, security, and control of private cloud. This provides midsized customers unified management and operations, one-click simplicity, intelligent automation, and always-on availability across multiple clouds. Nutanix's product portfolio includes Nutanix Cloud Infrastructure (NCI), Nutanix Cloud Manager (NCM), and Nutanix Database Service.
PacketFabric

PacketFabric's platform simplifies its midsized clients' network infrastructure with ease and speed of deployment of high-speed cloud and data center connectivity via an easy-to-use web portal. The company's offerings include Hosted Hybrid Cloud Connectivity, Point-to -Point Network Backbone Connectivity, and Flexile Data Center Interconnectivity.
Palo Alto Networks

Palo Alto Networks is shaping the cloud-centric future with technology that is transforming the way people and organizations operate. Its mission is to be the cybersecurity partner of choice, protecting our digital way of life. Palo Alto helps address the world's greatest security challenges with continuous innovation that seizes the latest breakthroughs in artificial intelligence, analytics, automation, and orchestration. By delivering an integrated platform and empowering a growing ecosystem of partners, Palo Alto Networks is at the forefront of protecting organizations across clouds, networks, and endpoints. The company's vision is a world where each day is safer and more secure than the one before. Among its midmarket offerings are its Next-Generation Firewalls, SASE, and XDR/MDR.
"Palo Alto Networks brings enterprise class security to the midmarket, helping customers achieve better security outcomes through consistent security management across all elements of their businesses, network, security operations and endpoint, as well cloud, multi-cloud and hybrid cloud environments. Our go-to-market approach of leveraging channel, ecosystem and service provider partners helps us scale to address midmarket security needs through managed service offerings, full platform designs, purpose built bundles and ala carte offerings. This ensures that the unique needs of midmarket companies of all sizes are met and can benefit from the completeness of the Palo Alto Networks portfolio."
Pappsales.com

Pappsales offers a comprehensive sales management solution that is affordable and easy to use. Unlike other sales management tools, Pappsales does not require clients to use Salesforce, which can be costly and complex for mid-sized businesses. Pappsales is designed to streamline sales processes, increase efficiency, and provide valuable insights that enable businesses to make data-driven decisions. Additionally, Pappsales offers a mobile app that allows sales teams to manage activities, optimize visits, and track performance from anywhere, at any time. In addition to the Pappsales platform, it offers a mobile app for field sales, and Salesforce automation.
"We are empowering midmarket companies to accelerate their sales process of sales force automation, and our strategy is reach out companies that have complex sales process and as Salesforce Partners help those companies to get to the next level of sales operations."
Perception Point

Perception Point is a leading provider of AI-powered threat prevention solutions that safeguard the modern workspace against sophisticated threats. The unified security solution protects email, web browsers, and SaaS apps, preventing phishing, BEC (Business Email Compromise), ATO, malware, spam, insider threats, data loss, zero-days, and other advanced attacks before they impact the end-user. Uniquely combining the most accurate threat detection platform with an all-included managed incident response service, Perception Point reduces customers' IT overhead, improves user experience, and delivers deep-level cybersecurity insights. Deployed in minutes, with no change to the organization's infrastructure, the easy-to-use cloud-native service replaces cumbersome, traditional point systems. It offers email, browser, and collaboration app security.
"Perception Point's AI-powered advanced threat prevention solutions help organizations protect more and manage less. This is especially relevant for mid-size companies who must strengthen their security posture with limited, overwhelmed security resources. Its solution delivers email, browser and SaaS app security, preventing all threat types including social engineering, file and URL-based threats, malicious insiders, and data leaks with a 99.95 percent detection rate. The solution includes a 24/7 IR service which manages the platform for the organization or MSP. The service optimizes detection, hunts for new threats, remediates incidents, and handles user requests, saving up to 75 percent of required SOC resources."
Performive

Performive, specializes in partnering with growing mid-sized companies by delivering secure, VMware-based cloud and security solutions, along with on-demand engineering resources and 24/7/365 customer support. To meet customers' needs, its infrastructure portfolio has expanded offering fully managed cloud, data protection and security solutions. With 20 data center locations across the globe, medium-sized businesses now have the global reach they need to deliver quickly and operate with efficiency. With Performive managing and strategizing their secure cloud operations, its customers' IT teams are now fully focused on driving innovation and business solutions in this demanding, ever-changing, technology-focused era. Performive's midmarket products and services include business continuity and disaster recovery, dedicated private cloud, and remote workforce enablement (remote monitoring and management, desktop as a service, VDI).
"Performive's midmarket strategy focuses on catering to the needs of midsize businesses, aiding in their expansion efforts. Leveraging our bespoke managed service provider solutions, we deliver tailored services that mirror enterprise-level support, empowering clients to grow without the burdensome costs associated with larger enterprises."
Pillir

Pillir application suites allow companies to instantly modernize their business functions and processes using out-of-the-box, pre-built web, and mobile-friendly business applications, easily customizing them to their unique needs while incurring a fraction of the resources, risk, cost, and time, of traditional methods. Based on Pillir's award-winning low-code platform, the suites comprise tens of different applications such as goods issue apps, goods receipt apps, stock transfer, transfer order, and many other common functions. The suites of business applications can be deployed in hours, giving enterprises an immediate solution to supply chain delays, rising costs, and their inability to respond to market needs.
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Proofpoint
Proofpoint, Inc. is a leading cybersecurity and compliance company that protects organizations' greatest assets and biggest risks: their people. With an integrated suite of cloud-based solutions, Proofpoint helps companies around the world stop targeted threats, safeguard their data, and make their users more resilient against cyberattacks. Leading organizations of all sizes, including more than 85 percent of the Fortune 100, rely on Proofpoint for human-centric security and compliance solutions that mitigate their most critical risks across email, the cloud, social media, and the web. The company's product portfolio includes Proofpoint Threat Protection, Proofpoint Information Protection, and Proofpoint Intelligent Compliance.
"Proofpoint's mission is to protect people and defend data. Our strategy is to provide the most comprehensive, AI-powered human-centric security solution to protect organizations across the four dimensions of human risk: threat risk, impersonation risk, identity risk, and data loss risk. We empower security teams with the visibility, efficiency, and tools they need to manage and address human risk factors more effectively. We continuously evolve our solutions based on customer feedback, industry trends, and emerging threats identified by our Threat Research team. Our platform is available to all midmarket customers through our numerous channel partnerships and managed service providers."
Protera
Protera is a leading authority in enterprise digital transformation. For 25 years, its mission has been to empower enterprises to achieve their modernization objectives with improved value, increased quality, and reduced risk. As the next-generation cloud modernization company, Protera's full suite of services range from IT strategy and design to implementation and management. Protera is a global SAP partner certified in BTP (Business Technology Platform) operations for RISE with SAP, hosting, cloud, application management, global outsourcing, SAP S/4HANA and SAP HANA operations services. The company provides enterprise workload migration to AWS, Microsoft Azure, or Google Cloud; comprehensive enterprise cloud managed services on any hyperscaler leveraging Protera CloudVantage (Security, FinOps, Modern Work); and SAP specific cloud and application services (migration, technical application management, complete SAP Basis support, RISE with SAP).
"We serve midmarket companies in North America across manufacturing, CPG (consumer packaged goods), oil, gas, energy, finance and health care industries. Growing midmarket enterprises consistently expect visibility, trust, security and cost efficiency from their mission critical business systems and strategies. We bring over 25 years of managing, securing and optimizing SAP and surrounding enterprise workloads for midmarket customers. Combined with our deep hyperscale partner engineering relationships, Protera's comprehensive and centralized cloud modernization and management solutions, processes and insights enable cost-effective, differentiated outcomes for all stakeholders."
QS2 Point

QS2 Point is a go-to partner for software and application development across North America. Headquartered in Traverse City, Mich., its extensive network of over 300 talented developers and experts in diverse tech platforms is strategically distributed across various centers in the Americas. QS2 Point offers software development, Salesforce support, administration and development, and data analytics.
"We specialize in offering team augmentation tailored specifically for the IT departments of midmarket enterprises. Within the midmarket segment, companies often face a critical decision: Should their technology teams prioritize innovation or maintenance? Our approach is designed to alleviate this dilemma. By taking charge of the maintenance aspect of their technology operations, we enable their teams to dedicate their efforts to innovation and core business strategies. We aim to provide an unparalleled, consistently excellent customer experience, ensuring our midmarket clients receive predictable, high-quality service. This strategic approach fosters long-term partnerships, supporting sustainable growth and a competitive edge."
Red Hat

Red Hat is a leading provider of enterprise open-source solutions, including Linux, cloud, container, and Kubernetes, delivering hardened solutions that make it easier for organizations to work across platforms and environments, from the core datacenter to the network edge. Red Hat believes that collaborative communities of experts create the best open source, IT and customer experiences. With this open-source spirit, Red Hat has established a robust partner ecosystem of industry leaders that can solve customer challenges, build integrated solutions and deliver transformative services. Its portfolio includes Red Hat Enterprise Linux, Red Hat OpenShift, and Red Hat Ansible Automation Platform.
"Customer first, partner always. Red Hat focuses on a sales culture that is customer-centric and partner sales-led, and we extend our go-to-market model with and through partners in order to be the scale engine for the company. In the midmarket, we execute on this partner-led vision by embedding services partners into each customer account in order to drive customer life cycle value, delivery and consumption."
Safetica

Safetica is a global software company that provides data loss prevention and insider risk management solutions to organizations of all sizes worldwide. Whether deployed on-premises or in the cloud, its solution is designed to protect business-critical data against accidental leaks and intentional theft in today's hybrid landscape.
"We envision a world in which all companies, large and small, can focus on their business without worrying about data loss and insider threats. We believe data protection should make running your business easier, not harder. Thanks to our expertise, our solution is simple and effective."
Scale Computing

Scale Computing is a leader in edge computing, virtualization, and hyperconverged solutions and delivers a complete platform for running applications at the branch office, distributed enterprise, and edge computing. Using patented HyperCore technology, Scale Computing Platform automatically identifies, mitigates, and corrects infrastructure problems in real-time, enabling applications to achieve maximum uptime, even when local IT resources and staff are scarce. When ease-of-use, high availability, and TCO matter, Scale Computing Platform is the ideal infrastructure platform for organizations of any size, across all verticals and industries. In addition to the Scale Computing Platform and Scale Computing HyperCore, it offers Scale Computing Fleet Manager.
"Scale Computing understands the unique concerns many midsize organizations face in today's challenging IT and economic landscape, including limited budget and resources. Whether a company has one IT administrator or hundreds, Scale Computing infrastructure eliminates complexity, lowers costs, and frees up management time. Using an appliance-based approach to virtualization, the Scale Computing infrastructure solution is faster to deploy, easier to manage, and allows organizations to scale seamlessly as they grow. Even in an emergency with the failure of hardware components or entire appliances, Scale Computing keeps critical apps up and running, providing midsized organizations the reliability and flexibility they need."
SECNAP Network Security

SECNAP Network Security is a managed security service provider (MSSP) and a cybersecurity research and development company. Since 2001, it has been combining human intelligence with innovative technology to protect SMBs to midmarket enterprises organizations and government agencies against cyberattacks. It offers CloudJacketXi -- a managed security-as-a-service platform (includes 24/7 SOC with standard and premium tiers), internal vulnerability assessments, and web application assessments.
"We are continuously researching, developing, and deploying the most advanced cybersecurity technologies, solutions, and services to combat current, new, and emerging threats. Our proprietary solution, CloudJacketXi, was designed for the unique needs of SMBs to midmarket enterprises. Our managed security-as-a-service platform provides an all-encompassing cybersecurity solution that matches the robust defenses used by Fortune 500 companies today."
SecureW2

SecureW2 offers a cloud-native solution for customers looking to power network security via Azure AD, Okta, and Google. While certificate-driven network security & WPA2-Enterprise security were initially reserved for large enterprises, with advancements in technology and the growing risk of credential theft, SecureW2 has made passwordless network security available for midmarket enterprises. SecureW2 delivers enterprise-level network security without enterprise-level cost or complexity. The SecureW2 platform offers comprehensive and cost-effective passwordless securing, including EAP-TLS, certificate-based 802.1X for wi-fi security, managed device auto-enrollment gateways, and a dynamic Cloud RADIUS solution focused on ease of deployment and user experience.
"SecureW2 offers midmarket-friendly cost and licensing models to help midmarket enterprises maximize ROI on their security spend. Its self-service pricing tool let MESes customize a solution based on their unique needs. A big focus in SecureW2's product development has been to make implementation, adoption, and ongoing maintenance as easy as possible for midmarket customers who have a very lean IT team. SecureW2 covers: PKI/Certificate services, RADIUS authentication, managed/unmanaged BYOD device, onboarding SSL inspection, Yubico Smart Card enablement, guest and IoT services, role-based access control, pre-shared key elimination, solving wi-fi credential theft, multi-tenant RADIUS for MSPs, and certificate-based VPN enablement."
Secureworks
Secureworks provides cybersecurity analytics, detection and response services. Its flagship offering, Secureworks Taegis, is a cloud-based cybersecurity analytics platform providing real-world threat intelligence and research.
SEI

SEI, a technology and investment solutions provider, has spent two decades developing cybersecurity capabilities to protect its own highly regulated business. By combining industry-leading enterprise technology and threat intelligence with proprietary systems, SEI has built a robust program designed to monitor, detect, analyze, and remediate existing and emerging cyber threats. SEI's job is to manage the cybersecurity program it constructs for clients and communicate what and how SEI is mitigating and remediating potential threats. SEI Sphere's cybersecurity solution combines industry-leading enterprise technology with proprietary tools, creating an intelligence-driven platform designed to monitor, detect, analyze, and remediate existing and emerging threats.
"Many SMBs don't have the resources to maintain a robust, in-house cyber program. As an MSSP to small-to-mid-sized businesses, SEI Sphere delivers enterprise-grade cybersecurity services that are right-sized and cost-effective for financial advisers, remote workforces, and other smaller organizations. The company's goal is to meet these clients where they are. The solution includes: comprehensive protection -- from laptop to email to web, a centralized security database, constantly refined cyber threat intelligence (CTI), and tenured security analysts defending digital environments with 24/7/365 monitoring and response. SEI Sphere also assists with cloud migration, providing SMBs with greater IT flexibility and business continuity."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Starburst

Starburst works well for midsized clients because it provides a single point of secure access to all their data, making it fast and easy to access no matter where it lives. Typically, organizations have multiple data repositories and architecture types. Without a single point of access, data users often need to spend valuable time and resources copying and moving data. Starburst, built on open-source Trino (formerly PrestoSQL), is the fastest SQL-based MPP (Massively Parallel Processing) query engine. It queries data across any database, making it instantly actionable for data-driven organizations. With Starburst, teams can lower the total cost of their infrastructure and analytics investments, prevent vendor lock-in, and use the existing tools that work for their business. Its product offerings include Starburst Enterprise and Starburst Galaxy.
Syncari

Syncari offers a no-code platform that does enterprise level data and process automation, geared toward business users. With Syncari, business users can have powerful data and workflow capabilities to drive GTM alignment, activation, and analysis for their business. Syncari is priced to be high value to midmarket and enterprises. The Syncari Embedded product allows OEMs to also deliver superior stateful sync of top business systems to drive alignment, activation, and analysis within their products.
Synology

A longtime leader in storage and backup solutions, Synology's expansive product lineup includes offerings for the midmarket. Some of them include Network Attached Storage devices, rackmount servers, backup and cloud services, and surveillance solutions. Synology's top midmarket offerings include Synology's File Storage Solution, Synology's Surveillance Solution, and Synology's Backup & Recovery Solution.
"Synology Active Backup Suite provides comprehensive backup and recovery solutions for physical servers, virtual machines, PCs, and cloud services. It includes features like data deduplication, incremental backups, and instant restoration to ensure data integrity and minimize downtime. Designed for SMBs and enterprises, it offers centralized, automated management and scalability without licensing fees on compatible Synology NAS models."
Syxsense

Syxsense's tiered product portfolio offers a range of pricing and functionality to meet the wide-ranging needs and growth of midmarket enterprises. Its foundational offering, Syxsense Manage, provides robust device and patch management capabilities, including discovery, patch scanning and deployment, feature updates and Active Directory integration, real-time data for compliance reporting and accurate decision-making, and troubleshooting tools such as remote control. As midmarket organizations grow, additional capabilities provide greater security while leveraging automation to enable companies to cover their IT infrastructure without needing additional staff or resources. With its product offerings, enterprises get vulnerability scanning, policy-based controls, and no-code automation technology -- Cortex -- that simplifies complex processes. Clients can create Cortex workflows, set them, and focus on more critical initiatives. With Syxsense Enterprise, clients can access pre-built scripts to remediate any vulnerabilities that are found in their security scans and this can be done automatically with Cortex.
Tech9

Tech9 provides experienced people, processes and technology at affordable prices. Its engineers, designers and project managers are all senior level. Every team follows a rigorous process to ensure they are correctly structured and the company uses best practice tools including AI to help build QA and design custom software. Tech9 offers its Tech9 Teams product, UX design, and staff augmentation.
TechSee

TechSee helps companies enter the digital visual transformation age, by increasing [customer satisfaction and net promoter score] all while lowering employee turnover and friction -- key things midmarket organizations are focused on. Its products and services include TechSee Live, Visual Intelligence, and Agent Assist.
"Market research shows that 56% of customers repeating themselves leads to high effort service with 40% of consumers saying poor service as a reason they cancel contracts. Mid-market companies can't afford to lose those customers because of something that is easily fixed with proper customer service. That is where TechSee comes in."
TechTrust

Midmarket organizations often have in-house talent that can do all the work that sellers in the supply chain do such as define functional requirements, needs analysis, and specifications. As a result, these organization may be paying for sales people and sales entities that they do not require. TechTrust remediates this by providing tech buying and tech talent services. The company will consult with an organization and assess their existing contracts, analyzing which ones qualify for a cash-back allowance. Organizations can then review the report, and choose which contracts they want to purchase through TechTrust.
Tenable

Tenable's exposure management solutions can help security practitioners prioritize efforts in remediating software vulnerabilities, misconfigurations and improperly assigned credential entitlements. Such comprehensive visibility and prioritization capabilities enable security teams to better understand their attack surface, eliminate blind spots and build a baseline for effective risk management. This empowers them to make the best decisions around what, when and how to mitigate exposures that put the organization most at risk. Its product portfolio includes Nessus Expert, Tenable Vulnerability Management (Formerly known as Tenable.io), and Tenable One.
"Midsized clients need full visibility into the attack surface along with a unified view of all assets. Tenable's exposure management solutions can help security practitioners prioritize efforts in remediating software vulnerabilities, misconfigurations and improperly assigned credential entitlements. Such comprehensive visibility and prioritization capabilities enable security teams to better understand their attack surface, eliminate blind spots and build a baseline for effective risk management. This empowers them to make the best decisions around what, when and how to mitigate exposures that put the organization most at risk."
ThreatLocker

ThreatLocker provides enterprise-level, endpoint security through its zero-trust product platform. ThreatLocker helps organizations globally implement controls that mitigate cyberattacks originating from downloaded malware, incoming network traffic, and the weaponization of trusted third-party applications. Among its offerings: application allowlisting, endpoint detection and response, and zero-trust endpoint security that satisfies compliance frameworks and cyber insurance requirements.
"Our strategy revolves around simplifying the implementation and scaling processes, ensuring that mid-market businesses can benefit from the robust security measures afforded by allowlisting. By leveraging innovative technology and easy to use interfaces, we strive to remove the complexities traditionally associated with allowlisting security solutions. In essence, our goal is to redefine allowlisting security by making it more accessible, user-friendly, and more supported than ever before."
Tintri by DDN

Tintri delivers purpose-built solutions to store and manage virtual machines in enterprise data centers. Organizations are looking for easy-to-use, robust and highly scalable data management solutions. These solutions should be quick to deploy, simple to manage, and deliver faster insights while maximizing the value of their complex, distributed data. Tintri consistently meets and exceeds the demands of virtualized workloads found in most data centers. With Tintri VMstore, businesses can accelerate development cycles, simplify management and predict every need as they scale. Its portfolio includes Tintri VMstore, Tintri Cloud Platform, and Tintri Cloud Engine.
"Tintri's solutions are designed with a broad appeal across market segments and industries. In terms of the midmarket segment, Tintri solutions are designed to deliver on simplicity in deployment and management with intuitive interface and management tools; performance and scalability in growing alongside midmarket business; cost-effectiveness and long-term ROI; and ensuring compatibility and integration with commonly used applications and IT infrastructure With its network of trusted channel partners, Tintri ensures midmarket customers are serviced effectively at multiple touchpoints. Robust and rapid customer services from Tintri and partners assist customers in deployment, management and troubleshooting data infrastructure."
The 2024 MES Midmarket 100: Top Companies Serving The Midmarket
MES Computing is proud to present this year's list of the key vendors and service providers serving the midmarket.
Tipalti

Tipalti provides a comprehensive, multi-entity accounts payable solution that automates the minutiae of supplier payment processes. Its customers typically wipe out 80 percent of their payables' effort, enabling them to focus on more strategic areas of the business while delighting their supplier base. Tipalti also helps improve compliance and financial controls, reduce risk, and employ best practices needed to scale. The company offers Tipalti PRO (finance/payables automation - advanced capabilities), Tipalti Procurement, and Tipalti Card (spend management).
TP-Link

TP-Link's Business/ISP solutions work well for mid-size clients because they meet their technical needs for new technology now that is affordable, and reliable with advanced features, remote management, easy to use interfaces, and ease of installation without the high cost of other midmarket networking solutions. TP-Link offers mid-size organizations access to Tier 1-quality chipsets and components while standing behind their solutions with limited lifetime warranties. It offers a slew of networking and surveillance appliances, and now, with its acquisition of Omada -- offers SDN (Software Defined Networking), as well as gateways, switches, access points, mesh routers and controllers.
Triton Networks

Triton helps businesses and organizations nationwide leverage critical changes in telecommunication technology to increase productivity, reduce operating costs, and protect the bottom line. Triton offers voice, data, networking, and cloud solutions that are customizable for a business' needs.
"At Triton Networks, we bring big ideas to midmarket businesses through a wide range of voice, data, and network solutions. We help clients work smarter, faster, and more efficiently with complete, business telecommunications solutions including reliable, secure business class Internet, local and long-distance phone services, web and email hosting, online backup and much more. Midmarket-bundled voice and internet service with just the right number of voice lines and bandwidth to best fit your business needs by providing business-class internet, voice and security services with best of class SLA's."
Twingate

Twingate offers a scalable solution designed for teams with shifting contractors/third-party users, the only zero-trust network access solution that does not require reworking, and pricing that matches that of current VPN technology (without the ongoing maintenance). The company also provides top-tier support for all customers regardless of spend/user counts.
Uprise Partners

Uprise Partners serves clients across the globe with a diverse approach tailoring IT and cybersecurity to meet the unique needs of midmarket businesses. With a focus on cybersecurity, cloud services and IT infrastructure management, Uprise Partners provides seamless integration and robust support tailored to each client. Its top products and offerings for midsize companies include managed IT services, cybersecurity solutions and cloud infrastructure management.
"Uprise Partners Managed IT Services are designed to provide midsize companies with reliable and efficient IT support. By offering 24x7 monitoring, proactive maintenance and rapid technical assistance, we ensure a stable and secure IT environment. Our services help businesses minimize downtime, optimize performance and focus on their core operations without worrying about IT-related issues"
Vercara

Vercara is a cloud-based security platform that provides layers of protection to safeguard businesses' online presence, no matter where attacks originate. Delivering the industry's highest-performing solutions and supported by 24/7/365 human expertise, growing midmarket brands depend on Vercara to protect their networks and applications against threats and downtime. Vercara's suite of cloud-based services is secure and reliable, ensuring that businesses and their customers experience exceptional interactions. Pressure-tested in tightly regulated and high-traffic verticals, Vercara's mission-critical security portfolio provides best-in-class DNS and application and network security (including DDoS, API, WAF, PDNS, and CDN) services to its 2,000-plus customers. Among the company's portfolio are UltraSecure, UltraDNS, and UltraDDR.
"Vercara's strategy involves providing purpose-built, best-in-class cybersecurity solutions tailored to the specific needs of mid-size companies. The security offerings are enhanced by the 24/7/365 white-glove services included with every purchase and around-the-clock access to a live SOC. The hands-on approach is particularly valuable for mid-size organizations that may not have dedicated in-house resources or expertise."
VIPRE Security Group

VIPRE delivers layered next-generation security solutions that protect everything from endpoints and email to end users. The company puts the latest technologies like machine learning and behavioral analysis to work for clients and partners focusing on simplicity without sacrificing the sophistication required to address today's threats. Regardless of IT team size, VIPRE solutions are lightweight as well as easy to implement and use. Its product offerings include VIPRE Email Security and VIPRE Security Awareness Training.
WatchGuard Technologies

WatchGuard Technologies is a global leader in unified cybersecurity whose mission is to be the security vendor of choice for MSPs. WatchGuard's Unified Security Platform architecture is uniquely designed for MSPs to deliver world-class security that increases their business scale, velocity, and improves operational efficiency. A 100 percent channel-focused organization, trusted by 17,000 security resellers and service providers to protect over 250,000 customers, WatchGuard's award-winning products and services span network security and intelligence, advanced endpoint protection, multi-factor authentication, and secure wi-fi. Together, they offer five critical security platform elements: comprehensive security, shared knowledge, clarity & control, operational alignment, and automation. Its product line includes WatchGuard MDR (managed detection and response offering), WatchGuard's line of Firebox firewall appliances.
"WatchGuard is recognized year-after-year for delivering industry-leading solutions and driving innovation in partner enablement. The company's strength comes from its focus on the partner community, which ranges from VARs to sophisticated MSSPs, though the sweet spot is MSPs who service the midmarket. MSPs need enterprise-grade security with a multi-tier, multi-tenant architecture that offers network security, endpoint, multi-factor authentication and secure wi-fi solutions that are deployed and managed from a single pane of glass. WatchGuard delivers these capabilities with its Unified Security Platform architecture, an approach that radically simplifies how MSPs protect customers, while enabling rapid, efficient, and profitable growth."
Workgrid Software

Workgrid was established with a mission to simplify work, improve efficiency, and enhance engagement through the use of intelligent technology. Workgrid simplifies the workday for employees and eliminates the time-consuming frustrations of searching for information and completing mundane tasks that disengage employees from meaningful work with a conversational AI assistant that serves as an employee's personal digital assistant, known as the Workgrid AI Assistant. The AI Assistant integrates across documents, business systems, and knowledge repositories to provide immediate answers, intelligent insights, and help employees accomplish tasks using a single, natural language interface.
"Workgrid targets companies of all sizes. For midmarket customers, we sell our conversational AI platform both directly to businesses and through channel partnerships, including referral and reseller partners. Our referral partners range from business and IT consultants to IT-focused software companies. Our reseller partners include intranet and digital workplace-focused software vendors who want to enhance their existing offerings with an AI Assistant. Our channel partnerships play an important role in Workgrid's midmarket strategy. By partnering with software vendors who specifically target the midmarket, Workgrid can expand its reach while leveraging our partner's existing brand reputation."
Zero Networks

Founded in 2019, Zero Networks is a unified platform for network segmentation, identity segmentation and secure remote access. Zero Networks' micro-segmentation offering is automated and MFA-powered to stop lateral movement and block ransomware. The Identity Segmentation solution provides unprecedented control of admin and service accounts, enabling the principle of least privilege. And the advanced ZTNA solution allows an enterprise to securely connect employees and vendors to its network, without compromising speed or performance. Offered on a single platform and user interface, Zero Networks is making true Zero Trust architecture a reality for enterprises of any size.
"Zero Networks serves the midmarket segment by offering a simple, comprehensive and user-friendly identity and network security solution. Our strategy focuses on addressing the specific needs and challenges faced by midmarket companies, such as limited IT resources, zero trust expertise and budget constraints. We offer a product suite that is fully automated and very easy to implement, dramatically reducing the complexity and headcount required for deployment and ongoing maintenance. And by providing agentless microsegmentation, identity segmentation, and advanced ZTNA products on a single, unified platform, Zero Networks ensures a simplified and efficient approach to network security. "